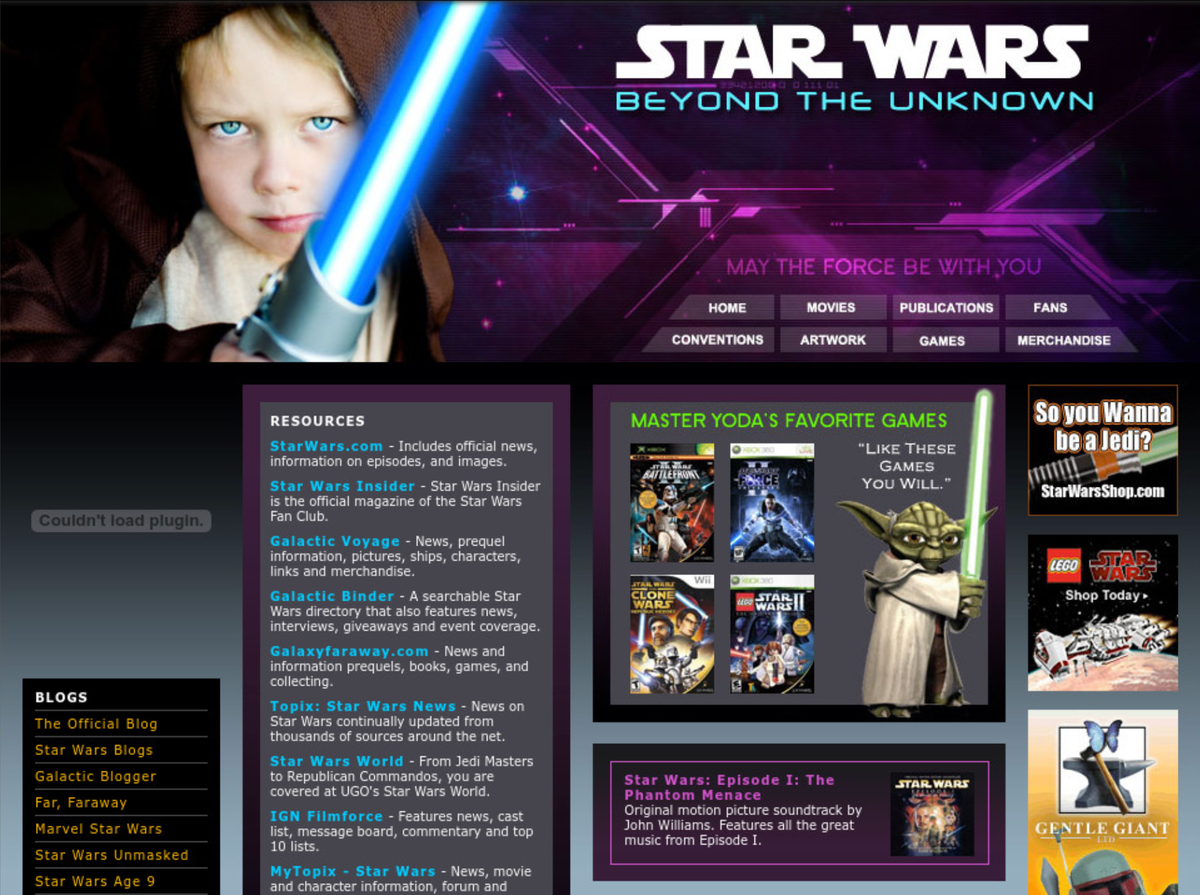
copy paste content plz
“Like these games you will,” the quote next to a cartoon image of Yoda says on the website starwarsweb.net. Those games include Star Wars Battlefront 2 for Xbox; Star Wars: The Force Unleashed II for Xbox 360, and Star Wars the Clone Wars: Republic Heroes for Nintendo Wii. Next to that, are links to a Star Wars online store with the tagline “So you Wanna be a Jedi?” and an advert for a Lego Star Wars set. The site looks like an ordinary Star Wars fan website from around 2010. But starwarsweb.net was actually a tool built by the Central Intelligence Agency (CIA) to covertly communicate with its informants in other countries, according to an amateur security researcher. The site was part of a network of CIA sites that were first discovered by Iranian authorities more than ten years ago before leading to a wave of deaths of CIA sources in China in the early 2010s. Ciro Santilli, the researcher, said he was drawn to investigating the network of CIA sites for various reasons: his interest in Chinese politics (he said his mother-in-law is part of the Falun Gong religious movement); his penchant for TV adaptions of spy novels; “sticking it up to the CIA for spying on fellow democracies” (Santilli says he is Brazillian); and that he potentially had the tech knowhow to do so given his background in web development and Linux. That, and “fame and fortune,” he said in an online chat. Santilli found other likely CIA-linked sites, such as a comedian fan site, one about extreme sports, and a Brazilian music one. In his own writeup, Santilli says that some of the sites appear to have targeted Germany, France, Spain, and Brazil judging by their language and content. “It reveals a much larger number of websites, it gives a broader understanding of the CIA’s interests at the time, including more specific democracies which may have been targeted which were not previously mentioned and also a statistical understanding of how much importance they were giving to different zones at the time, and unsurprisingly, the Middle East comes on top,” Santilli said. In November 2018, Yahoo News published a blockbuster investigation into the CIA’s covert communication channels and how they were exposed. That exposure originated in Iran before more than two dozen CIA sources died in China in 2011 and 2012, according to the report. The CIA ultimately shut down the covert communications tool. In September 2022, Reuters published its own investigation with the headline “America’s Throwaway Spies.” That article showed how, for example, a CIA informant in Iran called Gholamreza Hosseini was identified by Iranian authorities thanks to the CIA’s sloppily put together covert websites. One of the CIA’s mistakes was that the IP addresses pointing to the sites were sequential, meaning that after discovering one, it was straightforward for a researcher to find others very likely in the same network.
As the Reuters piece showed, typing a password into the ordinary looking websites’ search bar actually triggered a login process for sources to then communicate with the CIA. That Reuters piece published two domains, and described nine of the sites in total. The piece included clues that Santilli was able to use to find many, many more. Santilli found that the filenames of screenshots included in the article contained in some cases the URLs of the CIA sites themselves. He then looked them up on the Wayback Machine, he writes. He then used viewdns.info to find other related domains, a site that can show you what domains are associated with certain IP addresses.
Santilli’s own write-up goes into extensive detail on how he uncovered the Star Wars and other sites. It includes all manner of things like digging through a mass of historic domain names, analyzing the site’s HTML, and using “a small army of Tor bots” to bypass the Wayback Machine’s IP throttling. He says he did all this research without paying for any data, and instead used freely available online tools for his sleuthing. Citizen Lab previously identified 885 total websites following Hosseini telling Reuters the name of the site he used to communicate with the CIA, iraniangoals.com. Eventually Santilli had a few hundred domains which he manually inspected “as patience would allow,” he writes. Zach Edwards, an independent cybersecurity researcher, told 404 Media “The recent efforts to uncover the websites CIA used to communicate with their spies all over the world aligns with what I understood about this network. We’re now about 15 years past when these websites were being actively used, yet new information continues to drip out year after year.” “The simplest way to put it—yes, the CIA absolutely had a Star Wars fan website with a secretly embedded communication system—and while I can’t account for everything included in the research from Ciro, his findings seem very sound,” Edwards added. “This whole episode is a reminder that developers make mistakes, and sometimes it takes years for someone to find those mistakes. But this is also not just your average ‘developer mistake’ type of scenario.” About his research, Santilli said “At the very least the potential public benefit of enlightening history seems to be greater than that risk now. I really hope we’re right about this.” He added “It is also cute to have more content for people to look at, much like a museum. It’s just cool to be able to go to the Wayback Machine and be able to see a relic spy gadget ‘live’ in all its glory.” The CIA did not respond to a request for comment.